If you work in the constantly changing field of cybersecurity, you have probably heard of the “Google Cybersecurity Certification.” We will go into great detail about this certification in this lengthy post, discussing its importance, curriculum, salient points, and the various ways it can improve your knowledge of the field of digital reference.
Importance of Cybersecurity Certification
The significance of cybersecurity is greater than ever in a time when cyber dangers are always threatening the digital world. Certifications such as the Google Cybersecurity Certification are becoming more and more valuable as organizations throughout the globe actively seek out skilled experts who can protect their digital assets.

Overview of the Google Cybersecurity Certification
What’s That?
A specialized program called the Google Cybersecurity Certification is meant to give people the abilities they need to effectively defend against online attacks. Whether you work in the area currently or are just starting out, this certification provides a thorough curriculum to advance your knowledge.
Important Elements
This certification is notable for emphasising practical learning. Participants acquire a thorough understanding of cybersecurity concepts and the capacity to apply them in a professional setting through hands-on labs and real-world scenarios.
Getting Around the Curriculum
Cybersecurity Foundations
Starting with a strong foundation in cybersecurity principles, the journey begins. Threat detection, network security, and encryption are among the subjects discussed. This module guarantees that participants understand the core ideas that serve as the cornerstone of efficient cybersecurity procedures.
Google Cloud Security
It is crucial to comprehend how to secure data and apps in the Google Cloud environment because of the growing dependence on cloud platforms. The integration of Google Cloud Platform tools for creating strong security architectures is examined in this session.
Handling Incidents
One of the most important aspects of cybersecurity is being ready for anything. This session explores incident response and gives professionals the tools they need to properly address and mitigate security events.
Final Project
The certification programme culminates in a capstone project that requires participants to apply their acquired knowledge in a practical setting. This demonstrates their abilities and gives them invaluable experience in dealing with cybersecurity issues.
Benefits of the Certified Google Cybersecurity Professional Degree
Industry Acknowledgment
This accreditation is greatly enhanced by Google’s renowned standing in the IT sector. The abilities acquired through this programme are valued and recognised by employers throughout the world, making certified professionals in high demand.
Career Possibilities
Obtaining the Google Cybersecurity Certification can lead to a multitude of professional opportunities. This certification opens you a wide range of options, regardless of your interest in cybersecurity analysis, ethical hacking, or other professions in the field.
Testimonials and Success Stories
Actual Impact
Let’s examine real-world success stories to gain a true understanding of the value of the Google Cybersecurity Certification. Program graduates talk about their experiences and how getting the certification helped advance their professions.
Testimonial 1: Cybersecurity Expert from Aspiring Novice
A participant in the certification program, John Doe, describes his amazing journey from an aspirational novice to a skilled cybersecurity specialist. He gained practical skills from the hands-on labs and real-world circumstances that have greatly impacted his work.
Testimonial 2: Safely Using the Cloud
Cloud security enthusiast Jane Smith highlights how the Google Cloud Security module changed her life. Her career took a turn for the better as she realized how to secure data and apps in the Google Cloud environment.
Explore More Protecting Network Security through Data Protection
Overcoming Obstacles
Taking Care of Common Issues
Notwithstanding the certification’s extensive scope, candidates could run into difficulties. This part guarantees a seamless learning process by addressing typical issues and providing advice on how to get past roadblocks.
First difficulty: managing time
It can be difficult to juggle employment, personal obligations, and the certification program. Discover efficient time-management techniques to maximize your educational experience.
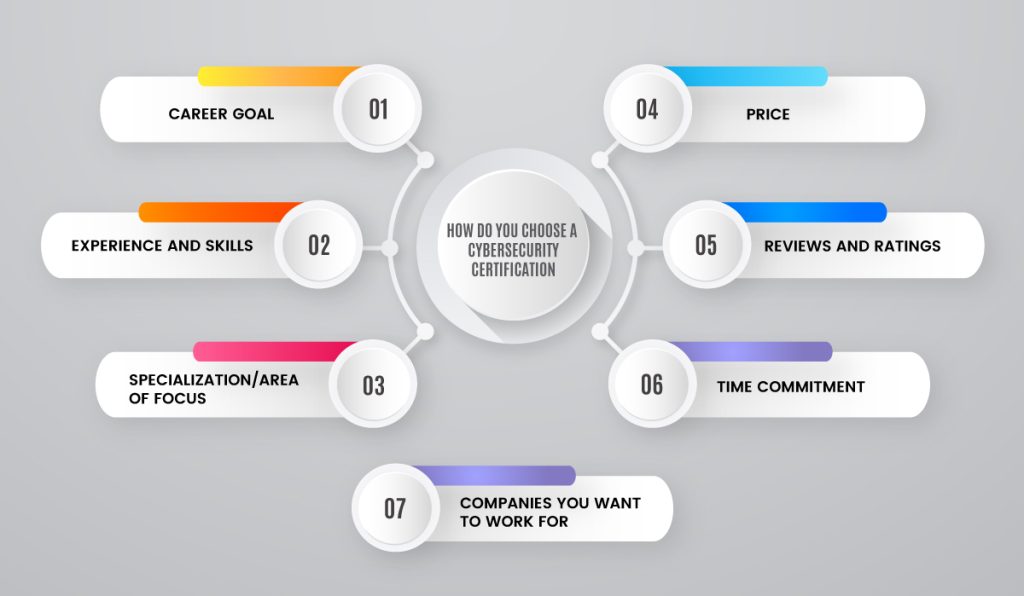
Comprehensive Examination of the Curriculum
Module 1: A Comprehensive Overview of Cybersecurity Foundations
Now let’s examine the basic module in more detail, looking at advanced threat detection methods, network security protocols, and encryption algorithms.
Describing Encryption
Discover the nuances of encryption, from historical cyphers to contemporary encryption techniques. Recognize how encryption serves as the foundation for safe communication.
Protocols for Network Security
Explore the realm of network security protocols, looking at how intrusion detection systems, firewalls, and secure communication channels help to protect digital networks.
Advanced Methods for Detecting Threats
Examine cutting-edge techniques for detecting threats, such as those based on machine learning, anomaly detection, and signature-based detection systems.
Module 2: A Strategic Approach to Security in Google Cloud
A strategic overview of data and application security in the Google Cloud environment is given in this section.
Making Use of Google Cloud Platform Tools
Learn how the tools available on the Google Cloud Platform are essential for creating strong security architectures. Learn about protecting your cloud infrastructure, from encryption at rest to identity and access control.
Cloud Security Case Studies
Examine actual case studies of businesses that have effectively implemented security measures in the Google Cloud. Take what you can from their experiences and incorporate it into your own work.
Module 3: Handling Unpredictability in Incident Response
Response to incidents is a vital component of cybersecurity. An extensive manual for efficiently managing and mitigating security events may be found in this section.
Formulating an Incident Reaction Strategy
Discover the critical processes involved in developing a strong incident response plan. Learn to precisely traverse each stage, from initial detection to confinement and eradication.
Actual Simulations
Test your incident response abilities by participating in real-world simulations. These models offer a useful comprehension of the difficulties encountered during a cyberattack.
Capstone Project (M Module 4): Putting Knowledge to Use
At the end of the certification programme, participants can apply their knowledge in a real-world context through the capstone project.
Project Outline and Requirements
Recognize the capstone project’s parameters and extent. This section offers a successful route, covering everything from selecting a pertinent topic to presenting your findings.
Exhibition of Senior Projects
View examples of outstanding capstone projects completed by previous participants. Take in the variety of projects and find ideas for your own special project.
In summary
In summary, the Google Cybersecurity Certification proves to be an effective resource for anyone looking to work in the cybersecurity industry. Through the integration of both practical and theoretical knowledge, this certification equips professionals to tackle the constantly changing demands of the digital security domain.










