In the current digital era, cybersecurity is crucial since cybercriminals are posing ever more sophisticated dangers to organisations. The demand for effective cybersecurity analytics is growing as the volume and complexity of cyberattacks continue to climb. We go into the field of cybersecurity analytics in this in-depth tutorial, examining its complexities, difficulties, and function in protecting digital assets.
Analyzing Cybersecurity Analytics: Dissecting the Intricacy
The methods and tools used to identify, evaluate, and counteract cyber risks are collectively referred to as cyber analytics. Large volumes of data from diverse sources must be gathered and analyzed to spot trends, abnormalities, and possible security issues. Organizations may enhance their cybersecurity posture and proactively reduce risks by utilizing sophisticated analytics tools like machine learning, artificial intelligence, and behavioural analytics.
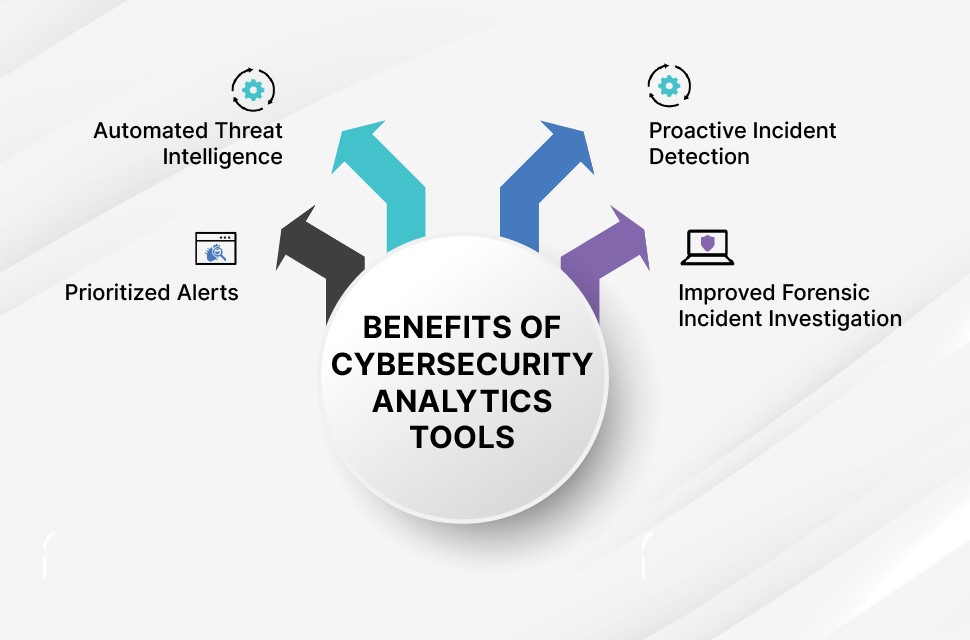
The Value of Analytics for Cybersecurity
Conventional security measures by themselves are no longer adequate to fend off the constantly changing cyber threat scenario. Organizations can use cyber analytics to quickly respond to security incidents, identify possible vulnerabilities, and detect threats in real-time. Network logs, endpoint devices, applications, and user behaviour data may all be analyzed to help organizations identify hidden risks and stop potential breaches before they happen.
Important Cybersecurity Analytics Components
A broad variety of methods and instruments created to address various cybersecurity issues are included in cybersecurity analytics. A few of the essential elements consist of:
Log Analysis
It is the process of looking through server, application, and network device logs to find unusual activity and security issues.
Endpoint Detection and Response (EDR)
Keeping an eye out for indicators of compromise on endpoint devices and quickly reacting to security problems.
Behavioural Analytics
Examining network traffic patterns and user behaviour to find abnormalities and possible security risks.
Threat Intelligence
It is the process of identifying both established and new cyber threats by utilizing external sources.
Artificial Intelligence and Machine Learning
Applying machine learning techniques to examine huge datasets and spot trends suggestive of security risks.
Difficulties with Cybersecurity Analytics
Despite its significance, cybersecurity analytics presents many difficulties for businesses.
Data Number and Complexity
It can be challenging to identify and properly address security vulnerabilities due to the sheer number and complexity of data produced by contemporary IT settings, which can overwhelm standard analytics techniques.
Lack of Skill
There is a deficiency in cybersecurity experts who possess the knowledge and abilities needed to handle and execute cyber analytics solutions.
Integration Difficulties
It can be difficult and time-consuming to integrate cybersecurity analytics technologies with the current IT architecture and security measures.
False Positives
Cyber analytics technologies have the potential to produce false positives, which could cause alert fatigue and possibly miss real security risks.
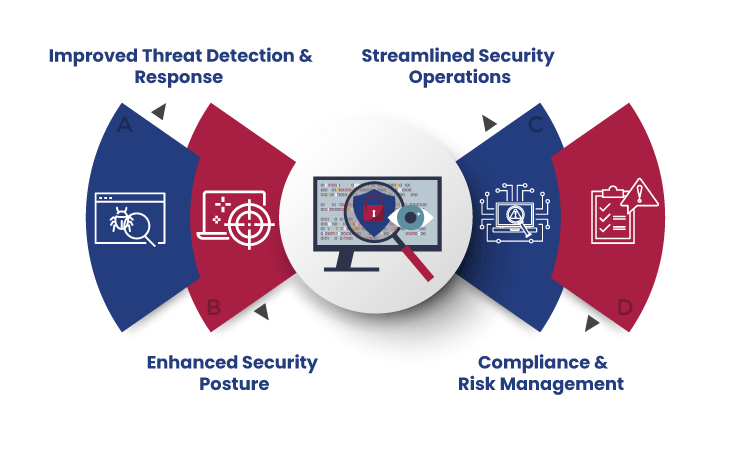
The Best Methods for Putting Cybersecurity Analytics into Practice
The following best practices should be taken into consideration by organisations to overcome these obstacles and maximise the efficacy of cybersecurity analytics:
Data Integration
To optimize visibility and coverage, make sure cybersecurity analytics technologies can interface with the current IT architecture and security policies.
Develop Your Staff’s Abilities
So they can use cybersecurity analytics tools efficiently, by investing in training and development initiatives. This will increase internal cybersecurity competence.
Continuous Monitoring
Put procedures in place for continuous monitoring to minimise the effects of cyberattacks by quickly identifying and responding to security concerns.
Threat Intelligence Sharing
Form alliances with other businesses and trade associations to exchange threat intelligence and work together on cybersecurity projects.
Explore More Guaranteeing Digital Safety: Cybersecurity Certification
FAQ’s
Cybersecurity analytics: what is it?
Data analysis methods are used in cybersecurity analytics to find, recognise, and address cyber threats. It includes a range of instruments and approaches for examining data from several sources and finding trends suggestive of security events.
What are cybersecurity analytics’ main advantages?
Real-time threat detection and response, enhanced security posture visibility, proactive vulnerability identification, and risk-based security resource prioritisation are some of the main advantages of cybersecurity analytics.
In cybersecurity analytics, what kinds of data are examined?
Network traffic logs, system logs, user activity logs, endpoint device data, application logs, and external threat intelligence feeds are just a few of the many types of data that cybersecurity analytics tools examine.
Conclusion
To sum up, cyber analytics is essential to defending companies against cyberattacks in the current digital era. Organizations may improve their cybersecurity posture, identify and address security issues instantly, and reduce the likelihood of data breaches and cyberattacks by utilizing advanced analytics techniques and tools. Organizations that prioritize investing in trained staff, technology, and best practices can effectively negotiate the complexities and fortify their cybersecurity defences, even in the face of obstacles offered by the complexity of cyber analytics.










